【Linux基础服务教程】httpd(Apache)配置https访问
一、网站传输协议
- http
- 80/tcp
- 数据以明文的方式传输
- https
- 443/tcp
- 数据以密文的方式传输
1.私有CA和公有CA
- CA是一个证书颁发机构,私有CA代表本地自己搭建的CA服务器,而公有CA属于互联网公认的CA认证机构
2.CA申请SSL证书流程
- 电商服务器生成证书申请【.csr文件】, 同时将电商服务器的公钥放入证书申请;将证书申请发送给CA
- CA审批信息, 通过后CA会使用自己的私钥进行签名;相当于签署证书【.crt】
- 客户端访问电商服务器时,服务器会将证书信息发送给客户端
- 客户端通过CA的公钥验证证书,验证通过后可获取电商服务器的公钥
- 客户端选取对称算法、密钥,使用公钥加密,发送给服务器、服务器解密
- 进行真实数据交互

二、配置公有CA颁发的SSL证书
1.域名注册
需要提前准备一个域名!!!
个人推荐的几个域名注册机构:阿里云万网、腾讯云、cloudflare
2.申请SSL证书
我这里拿腾讯云做演示
普通个人用户可以选择免费的证书
缺点:只支持主域名和www域名
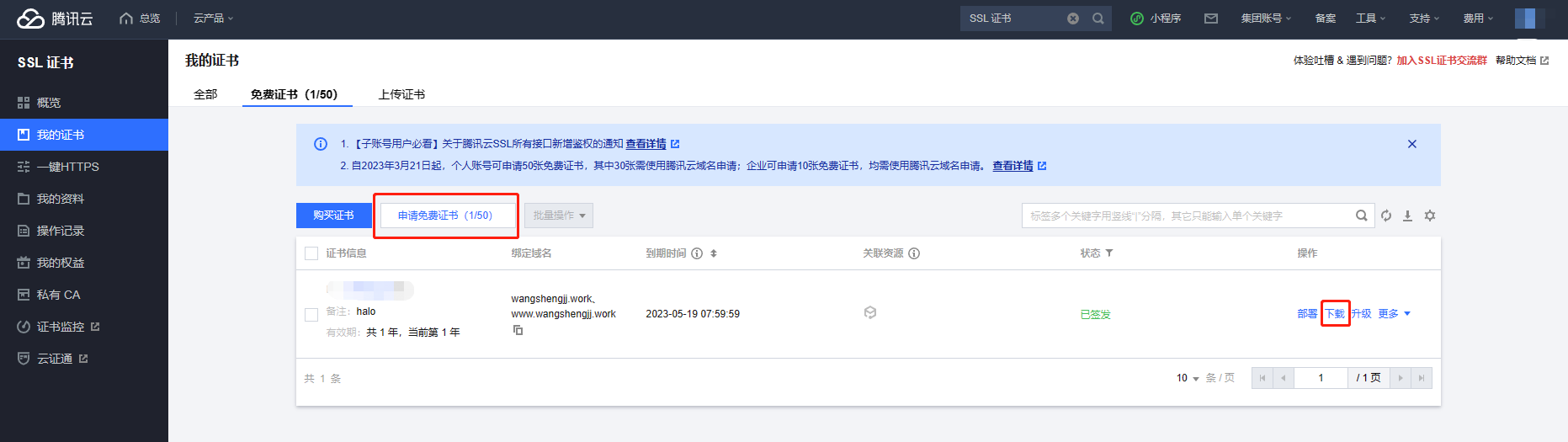
或者选择购买证书
个人推荐购买泛域名证书
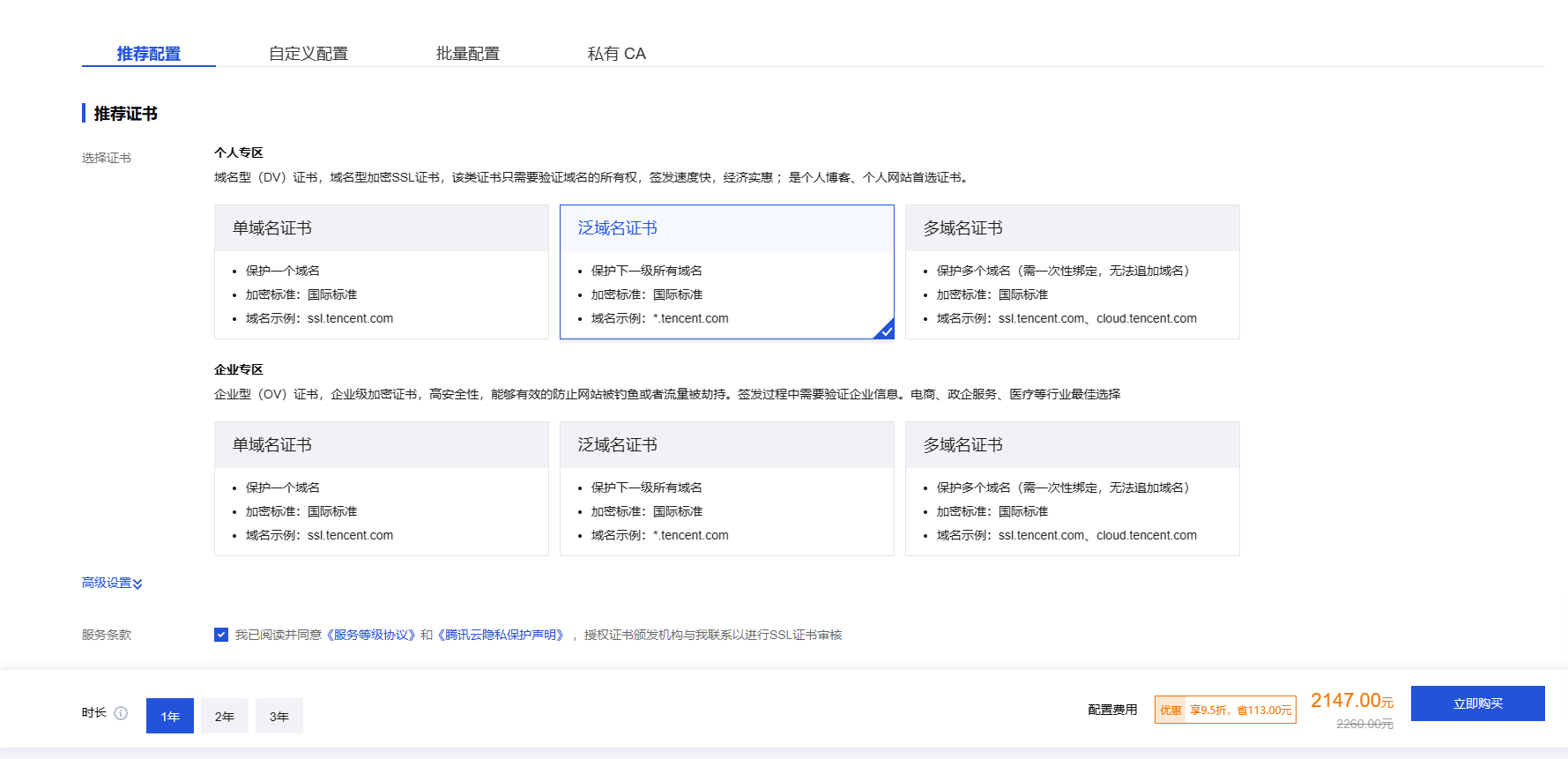
更或者使用Let’s Encrypt的免费证书
虽然只有3个月,但是支持自主续签
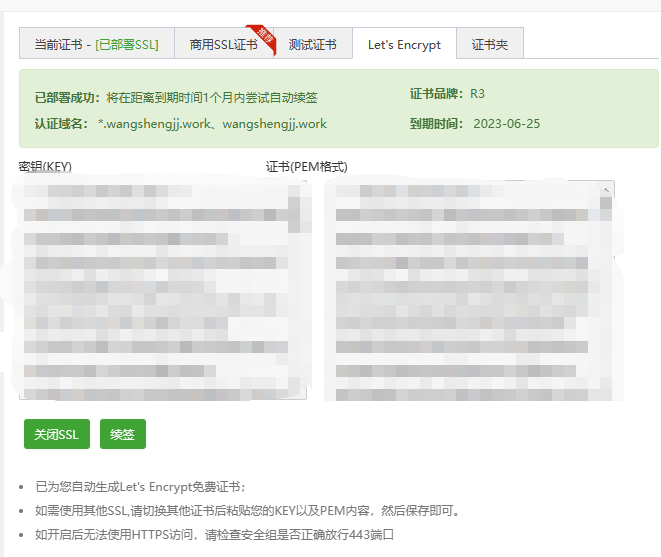
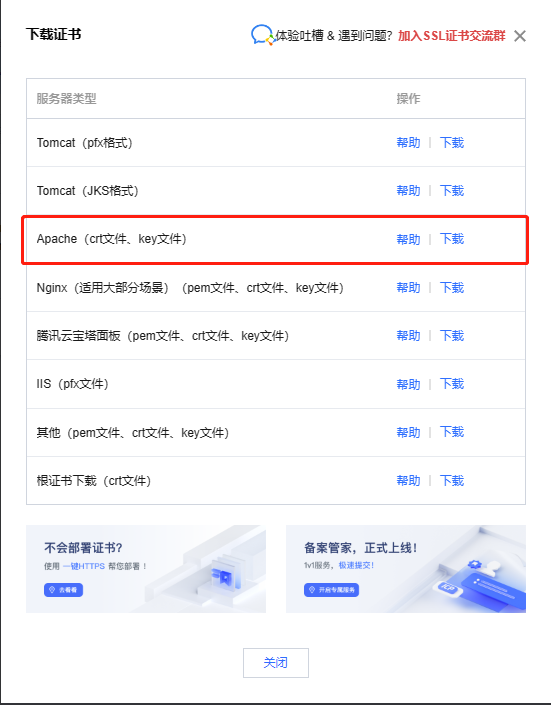
3.下载证书
- 目前学的是Apache,所以我们选择Apache证书
- 如果您使用的是其他类型服务器,比如Nginx请选择下载相应的证书
4.配置https访问
上一期教程虚拟主机
A.安装mod_ssl模块
[root@localhost ~]# yum install -y mod_ssl
B.配置基于https的虚拟主机
a.创建网页目录
[root@localhost ~]# mkdir -p /www/wwwroot
b.创建测试文件
[root@localhost ~]# vim /www/wwwroot/index.html
<h1>vivo50.wangshengjj.work</h1>
c.创建证书文件存放文件夹
[root@localhost ~]# mkdir /www/ssl
d.上传证书文件
上传过程省略
[root@localhost ~]# ls /www/ssl
rui.crt rui.key
e.编辑配置文件
[root@localhost ~]# vim /etc/httpd/conf.d/ssl.conf
....................上面的省略,不代表配置文件只有以下这些内容
<VirtualHost _default_:443>
# General setup for the virtual host, inherited from global configuration
DocumentRoot "/www/wwwroot" #网页目录
ServerName vivo50.wangshengjj.work:443 #域名
SSLCertificateFile /www/ssl/rui.crt #需要指定证书位置
SSLCertificateKeyFile /www/ssl/rui.key #需要指定秘钥文件位置
<Directory "/www/wwwroot">
Require all granted #给网页目录权限
</Directory>
</VirtualHost>
f.重启httpd(Apache)服务
[root@localhost ~]# systemctl restart httpd
C.测试
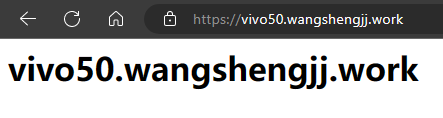
三、配置https自动跳转
自行把下面内容加入到http配置文件即可
RewriteEngine On
RewriteCond %{HTTP_HOST} www.linux.com [NC]
RewriteRule ^/ https://www.linux.com [L]
- %
- 调用客户端所访问的网站主机名
- [NC]
- 忽略大小写
- [L]
- 立即响应
四、单服务器多https网页
- 复制ssl.conf文件改名即可
- 注意:需要删除<VirtualHost default:443>之前的所有内容
- 原因:只需一个配置文件拥有配置即可
五、配置私有CA颁发的SSL证书
1.创建CA服务器需要的库文件
自行准备第二台虚拟机当做CA服务器
[root@ca ~]# touch /etc/pki/CA/index.txt
[root@ca ~]# echo 01 > /etc/pki/CA/serial
2.创建CA服务器需要的秘钥
[root@ca ~]# openssl genrsa -out /etc/pki/CA/private/cakey.pem 1024
Generating RSA private key, 1024 bit long modulus
..++++++
.....++++++
e is 65537 (0x10001)
3.颁发自签证书
[root@ca ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:china
string is too long, it needs to be less than 2 bytes long
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:bj
Locality Name (eg, city) [Default City]:bj
Organization Name (eg, company) [Default Company Ltd]:bj
Organizational Unit Name (eg, section) []:bj
Common Name (eg, your name or your server's hostname) []:ca.linux.com
Email Address []:bj@qq.com
[root@ca ~]# ls /etc/pki/CA/
cacert.pem certs crl index.txt newcerts private serial
4.在web服务器申请证书
回到web服务器
[root@web_server ~]# mkdir /etc/httpd/ssl
[root@web_server ~]# openssl genrsa -out /etc/httpd/ssl/www.linux.com.key 2048
Generating RSA private key, 2048 bit long modulus
......................+++
.....................................................................+++
e is 65537 (0x10001)
5.创建证书申请
[root@localhost ~]# openssl req -new -key /etc/httpd/ssl/www.linux.com.key -out /etc/httpd/ssl/www.linux.com.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn #注意这里的信息需要和CA服务器一致
State or Province Name (full name) []:bj #注意这里的信息需要和CA服务器一致
Locality Name (eg, city) [Default City]:bj #注意这里的信息需要和CA服务器一致
Organization Name (eg, company) [Default Company Ltd]:bj #注意这里的信息需要和CA服务器一致
Organizational Unit Name (eg, section) []:bj #注意这里的信息需要和CA服务器一致
Common Name (eg, your name or your server's hostname) []:www.linux.com #这里填写自己的域名
Email Address []:bj@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
6.证书发送给CA服务器
[root@web_server ~]# rsync -av /usr/local/nginx/ssl/www.linux.com.csr root@192.168.140.11:/tmp/ #IP为CA服务器
7.CA服务器签署证书
[root@ca ~]# openssl ca -in /tmp/www.linux.com.csr -out /etc/pki/tls/certs/www.linux.com.crt -days 3650 #证书有效10年
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jun 21 06:06:54 2021 GMT
Not After : Jun 19 06:06:54 2031 GMT
Subject:
countryName = cn
stateOrProvinceName = bj
organizationName = bj
organizationalUnitName = bj
commonName = www.linux.com
emailAddress = bj@qq.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
67:6D:B8:84:3A:5C:BE:99:81:4A:49:F4:CD:61:5E:8B:99:3B:EF:13
X509v3 Authority Key Identifier:
keyid:C8:EF:D2:FB:E8:D5:2B:50:D8:7C:07:7A:27:72:B5:D6:33:09:D6:56
Certificate is to be certified until Jun 19 06:06:54 2031 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
8.查看刚刚颁发的证书文件
[root@ca ~]# ls /etc/pki/tls/certs/
ca-bundle.crt ca-bundle.trust.crt make-dummy-cert Makefile renew-dummy-cert www.linux.com.crt
[root@ca ~]#
[root@ca ~]# cat /etc/pki/CA/serial #从01变成02
02
[root@ca ~]# cat /etc/pki/CA/index.txt
V 310619060654Z 01 unknown /C=cn/ST=bj/O=bj/OU=bj/CN=www.linux.com/emailAddress=bj@qq.com
9.将签好的证书送给web服务器
[root@ca ~]# rsync -av /etc/pki/tls/certs/www.linux.com.crt root@192.168.140.10:/etc/httpd/ssl
10.配置SSL证书
[root@localhost ~]# vim /etc/httpd/conf.d/ssl.conf
....................
<VirtualHost _default_:443>
# General setup for the virtual host, inherited from global configuration
DocumentRoot "/linux"
ServerName www.linux.com:443
SSLCertificateFile /etc/httpd/ssl/www.linux.com.crt #我们的证书文件都在这个目录下
SSLCertificateKeyFile /etc/httpd/ssl/www.linux.com.key
<Directory "/linux">
Require all granted
</Directory>
11.检查配置文件是否OK
[root@localhost ~]# httpd -t
Syntax OK
12.重启服务
[root@localhost ~]# systemctl restart httpd
13.查看端口
[root@localhost ~]# netstat -antp | grep http
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 7144/httpd
tcp6 0 0 :::443 :::* LISTEN 7144/httpd
- https基于443/TCP
14.浏览器测试访问
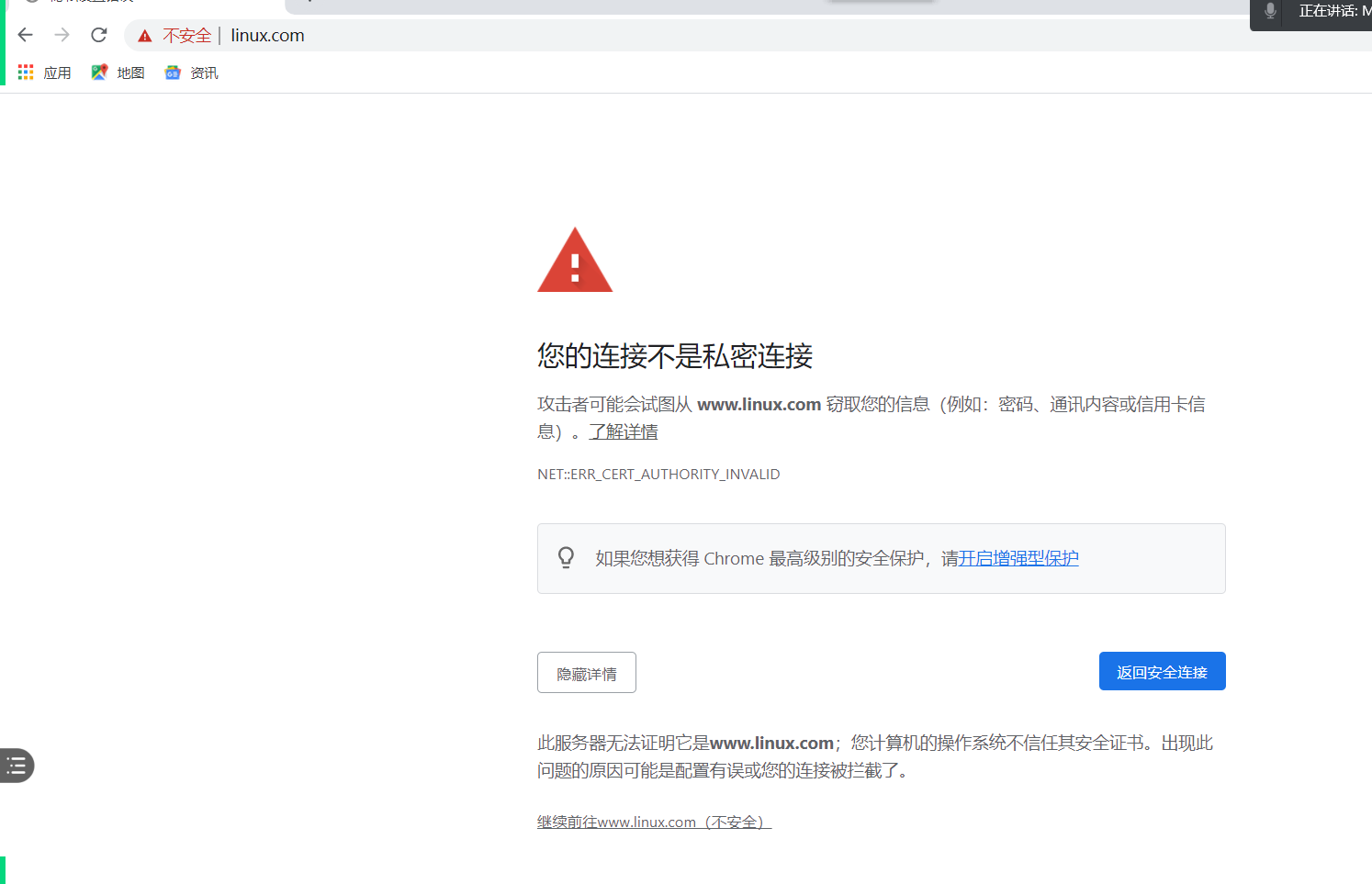
- 选择 高级-继续访问
- 报错原因:浏览器会自动查找网上的公有CA验证,因为我们是私有CA,没有在公网认证所以会有这个提示

